Difference between revisions of "Information: Kujenga"
(→Information Control) |
|||
| (27 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | <div style="font-size:0.9em; color:#333;margin-bottom:25px;" id="mw-breadcrumbs"> | |
| + | [[Africa|DATE Africa]] > [[Kujenga]] > '''{{PAGENAME}}''' ←You are here | ||
| + | </div> | ||
| + | <div style="float:right">__TOC__</div> | ||
| − | [[Kujenga]] information environment is somewhat dated with limited availability of | + | [[Kujenga]] ’s information environment is somewhat dated, with limited availability of internet, mobile phone, and television access for the general population. The government is investing in projects to expand internet connectivity but widespread public access is still limited. While Kujenga does have a mix of public and private media available, the government controls much of the media programs available to the public. Kujenga’s information operations utilize mostly low-tech capabilities, along with selected niche capabilities. As a less technically oriented country with narrowly focused modernization goals, information flow remains concentrated on widely available systems. Radio and print media still dominate the Kujenga information sphere. As a country with limited technical information systems, Kujenga is significantly less susceptible to cyber-attacks and information system manipulation. Kujenga’s government seeks to dominate the information sector by controlling the flow of information to the population. To maintain that dominance, the government plans to increase use of new technology and meter its release to the population. |
== Satellite Telecommunications == | == Satellite Telecommunications == | ||
| − | + | Kujenga’s satellite communication capabilities are currently limited to commercial products. Kujenga recently entered into contracts with a company from Torrika to provide a turnkey solution for micro-satellites. Kujenga’s goals are to enhance satellite communications services and to establish satellite-based SIGINT and IMINT capabilities by mid-2019. The contract specifies construction of satellite platforms to Kujenga specifications, launch, and a ground-control complex. Once operational, the satellites will provide Tier-1 command and control communications, signals intercept, and imagery. | |
== Navigation == | == Navigation == | ||
| − | Government and military forces have access to GPS | + | Government and military forces have access to GPS capabilities for critical command and control systems and weapons platforms. Limited availability causes Kujengan forces to rely on proven manual navigation techniques not dependent on satellite systems. Kujenga assigns forces on a regional basis for prolonged periods so they are very familiar with the terrain and its characteristics. |
== Public Communications Media == | == Public Communications Media == | ||
| − | + | Kujenga Telecommunications (KT) is the government monopoly controlling the country’s’ communication networks. Private investors can purchase franchises through KT to open businesses providing radio, television, and both wired and wireless internet services. KT provides radio and television and franchises private broadcast services. Contribution of the communication sector to the Kujenga economy is currently only at 2%, significantly below the 4% or higher found in other countries in the East Africa. Kujenga’s government, realizing the potential positive impact on the economy, instituted a strategy to expand services available to the public. As ICT developments come on line, the government expects to rapidly realize economic growth other developing countries experience. This strategy maintains a central requirement to monitor and control the information flow. | |
| − | The government intercepts and monitors private message traffic | + | The government intercepts and monitors private message traffic across all information systems. It conducts active suppression of media reports critical of the government through network filtering, as well as jamming or interruption of service for the targeted broadcast system. Anti-government activities in the Tanga and southwest region prompted the government to use active measures to disrupt or restrict information flow. The government uses jamming, internet filtering, and destruction of print media in both regions in efforts to suppress the information campaigns of insurgent groups. |
=== Internet === | === Internet === | ||
| + | [[File:Kujenga Fiber-Optic Backbone 2.png|thumb|402x402px| | ||
| + | Fiber-optic network including new construction. | ||
| + | ]] | ||
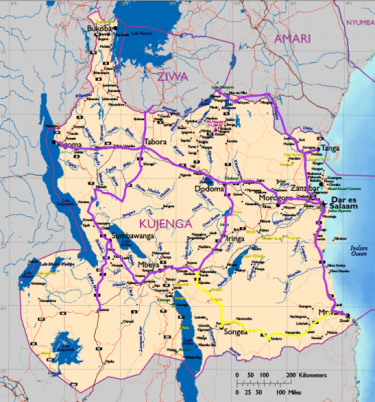
| + | Kujenga’s general population is not technically adept, but has a growing interest in the internet. At 12% penetration, Kujenga has one of the lowest teledensities in the world, largely based on government access restrictions. To maintain control of public information flow, the government methodically works to expand availability of internet access. The government also invests in expansion of the network backbone available in Kujenga. Consistent access is limited to those institutions and organizations that need it for modern business. The government expects the improved business access coupled with other economic development initiatives to help generate at least a 2% GDP growth. The ruling group enjoys mostly unrestricted internet access while the public is only beginning to establish regular connectivity. Internet availability for the public is limited to major cities, with individual access still prohibitively expensive for the average Kujengan. [[File:Internet Use DATE-Africa.png|left|thumb| | ||
| + | '''Kujenga is slowly expanding internet availability.''' | ||
| + | |400x400px]] | ||
| − | + | KT is laying the groundwork necessary to allow continued monitoring and control of Kujenga’s internet users. To facilitate this control, the government established the Network Security Agency (NSA) in 2011. The NSA not only issues national internet policies and guidance, but also develops the means to penetrate or block internet communication. The agency restricts targeted internet protocol (IP) addresses or domain names. It also uses deep-packet inspection (DPI) to identify email traffic deemed contrary to the governments’ interests. | |
| − | |||
| − | KT is laying the groundwork necessary to allow continued monitoring and control of | ||
| + | Kujenga’s government is widely known for its pervasive surveillance of online and mobile phone communications. A 2014 Human Rights Watch report accused Kujenga’s government of using cyber-attack methods to monitor and arrest citizens it deemed a threat. Human Rights Watch accused the government of using a monitoring system from the telecommunications firm Olvana Telecommunications Enterprise (OTE) to monitor various communications platforms, including phone and internet networks. OTE permits deep-packet inspection and the interception of emails on KT’s telecommunications network. KT also used ZSmart, a customer management database that provides the monitor with users' personal information, SMS text messages, and the ability to record phone conversations. The ZSmart program has the ability to GEOlocate a user's position by tracking mobile cellular devices. The full extent of the government's use of these technologies is unclear. The government, however, has produced emails, text messages, and phone calls as evidence during legal proceedings against bloggers and journalists. | ||
| − | + | ---- | |
| − | |||
=== Television === | === Television === | ||
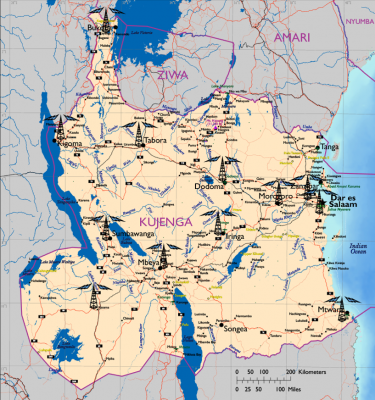
| − | [[File:Kujenga Television.png|thumb| | + | [[File:Kujenga Television Towers.png|thumb|400x400px| |
| − | + | Television tower locations in Kujenga. | |
| + | ]] | ||
| + | Television access is most common in urban areas. Kujenga is at the lower end of the scale of households with televisions. While slowly growing, the number of households with television currently stands at just over 9%, with a projected growth rate of .5% per year. Any television found in rural areas tends to be a family or tribal asset shared by the group. Some insurgent groups provide television access and programming to support their media strategy, as they provide not only programming of interest but also messages supporting their cause. | ||
| − | The religious programs recently caused a backlash from the Army of Justice and Purity (AJP) | + | Kujenga’s TV stations are both public/government granted private franchises. The government approves program content for public access. Broadcast programming comes from KT, and provides a variety of entertainment, news, sports, and pro-government political commentary. A recent addition of approved private broadcasters providing primarily religious programming is reaching both local and regional audiences. The focus of these broadcasts is to provide the poor and rural population with positive and encouraging programming. These religious programs recently caused a backlash from the Army of Justice and Purity (AJP), who seized a television station at Mbeya in order to broadcast their own message. The AJP stated that both government and private programs were an attempt to co-opt and dilute their message. They held the station and broadcast anti-government messages until overwhelmed by government forces. AJP media elements filmed the brutal and overwhelming government response, creating propaganda supporting its media message. The AJP continues to use all available media resources to carry its message to the Kujengan people. |
| + | === Radio === | ||
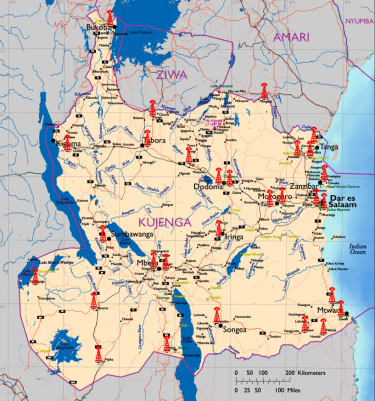
| + | [[File:Kujenga Radio Towers.png|left|thumb|401x401px| | ||
| + | Radio broadcast tower locations. | ||
| + | ]] | ||
| + | Until recently, the government monopolized the radio media environment in Kujenga. The public had no other conduits for independent news or other programming. The advent of pirate radio stations and powerful broadcasts by stations located in bordering countries expanded the public’s knowledge of differing views and perspectives on activities in Kujenga. Recognizing the growing public dissatisfaction with the media status-quo, Kujenga’s government initiated programs to license private radio broadcasts. The result of the program was an expansion from the single government radio network to 22 private broadcasters. Licensed private broadcast networks must follow stringent government controls and regulations, but the expansion is fueling growing public demands for unbiased and differing perspectives for news, sports, entertainment, and politics. | ||
| − | + | Public and private radio is the most ubiquitous information source available to the public. The government follows the same process with radio as it does with television. KT issues franchises for radio broadcast licenses and approves all programming content. By controlling the broadcast towers and monitoring program content, the government seeks to ensure a consistently positive government message. Deviations from the approved government content by private stations results in suspension of operating licenses for undetermined periods. | |
| − | |||
| − | |||
| − | + | The Free Tanga Youth Movement (FTYM) and Army of Justice and Purity (AJP) both utilize pirate radio in their respective regions to broadcast their anti-government message to the population. The government response is blanket jamming of the station signal, use of direction-finding equipment to pinpoint the transmitter locations, and eventually, permanent destruction of the broadcast sources. Faced with this threat from government forces, these groups utilize multiple mobile transmitters with limited broadcast range. | |
| − | |||
| − | The Free Tanga Youth Movement (FTYM) and Army of Justice and Purity (AJP) | ||
=== Print Media === | === Print Media === | ||
| − | Population literacy stands at over | + | Population literacy stands at over 73% so print media holds a very strong position in public information flow. As with the other information mediums, print media must conform to government censorship and monitoring. Of the 12 daily newspapers, 13 weekly newspapers, and 17 national magazines, it is almost certain that one or more of them will be in conflict with the government at any given time. |
| + | |||
| + | Print media is generally safe from government reaction when they run stories or reports of bureaucratic mismanagement or inefficiencies. However, reports of suspected corruption by specific ministers or senior leadership often results in shuttered offices for an indeterminate period. Once public attention dies down, government authorities usually allow the offending newspaper or periodical to resume operation. | ||
| − | + | Recalcitrant journalists that fail to conform to government guidelines often find themselves jailed under some, often obscure, aspect of the law. The Press Law of 1987 allows the government to suppress news reports or stories that are detrimental to national interests, modifying the constitutional guarantee of freedom of press. | |
| − | Recalcitrant journalists that fail to conform to government guidelines find themselves jailed under some, often obscure, aspect of the law. | + | |
| + | The growth of the internet and social media is pressuring physical print media businesses. Growth projections for mobile phones and internet access are driving the print media businesses and groups to expand their reach into the social media sphere. Printers are seeking additional markets to remain viable in the changing environment. Many are transferring their knowledge and skill in developing meaningful message products to the new information media. | ||
| − | |||
Government opposition groups are currently the most active users of social media. They use it to send handbills and infographic bulletins to followers and sympathizers in Kujenga, neighboring countries, and expatriates. To develop successful messages, the groups are working with print media companies to produce professional products. | Government opposition groups are currently the most active users of social media. They use it to send handbills and infographic bulletins to followers and sympathizers in Kujenga, neighboring countries, and expatriates. To develop successful messages, the groups are working with print media companies to produce professional products. | ||
| − | |||
| − | |||
=== Telephone === | === Telephone === | ||
[[File:Clayiphonemotofone-2.jpg|thumb|right|'''Significant Public Interest in Mobile Technology''']] | [[File:Clayiphonemotofone-2.jpg|thumb|right|'''Significant Public Interest in Mobile Technology''']] | ||
| − | If a Kujengan has a phone, it is a mobile phone. As with many other countries in Africa, the population generally bypassed fixed landline phones. Comparison of landline to mobile subscribers sees 1% and 25% per 100 citizens, respectively. Mobile subscribers are mostly the ruling elite, business leaders, and military leadership | + | [[File:Kujenga Cell Tower Coverage.png|left|thumb|400x400px| |
| + | General cellular phone coverage. | ||
| + | ]] | ||
| + | If a Kujengan has a phone, it is a mobile phone. As with many other countries in Africa, the population generally bypassed fixed landline phones. Comparison of landline to mobile subscribers sees 1% and 25% per 100 citizens, respectively. Mobile subscribers are mostly the ruling elite, business leaders, and military leadership. Major cities and urban areas have the greatest concentrations of mobile phone coverage, with limited coverage along the main roads between cities. Laws prohibit private satellite phones; government customs officers confiscate them at all entry points. | ||
| + | |||
| + | Kujengans are aware of the technological advancements in communication technology. Until recently, the government limited the expansion of the mobile phone networks available. The government views mobile technology as a threat to its control and direction of the population. It views outside attempts by groups in Amari and Ziwa to extend technology and information to the Kujenga population as a direct threat to its control and power. | ||
| − | + | Reports and studies show that mobile phone and internet access in African countries stands at over 1 billion. Projections suggest it will jump to 1.4 billion subscribers in the next 5 years. This led the Kujengan government to conclude that expansion is inevitable. That perceived inevitability is driving the government to take proactive steps to expand the mobile phone network while it can still control that expansion. | |
| − | |||
| − | Reports and studies show that mobile phone and | ||
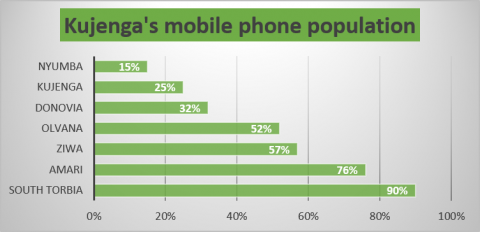
| − | Current subscriber levels are approximately 25%, which puts Kujenga a distant third behind Ziwa and Amari in mobile phone penetration of the population. The predicted availability of low-cost mobile phones, data packages, and the government expansion of available mobile networks creates the conditions for the subscriber population to exceed 50% by 2022. The government is not only expanding the mobile networks but also its capability to monitor and track citizen activities using COTS software and hardware. | + | Current subscriber levels are approximately 25%, which puts Kujenga a distant third behind Ziwa and Amari in mobile phone penetration of the population. The predicted availability of low-cost mobile phones, data packages, and the government expansion of available mobile networks creates the conditions for the subscriber population to exceed 50% by 2022. The government is not only expanding the mobile networks but also its capability to monitor and track citizen activities using commercial off-the-shelf (COTS) software and hardware. |
| − | + | [[File:Kujenga Mobile Population.png|center|480px|'''Low mobile phone penetration in Kujenga'''|frameless]] | |
| − | [[File:Kujenga Mobile Population.png|center|480px|'''Low mobile phone penetration in Kujenga''']] | ||
=== Postal/Courier === | === Postal/Courier === | ||
| − | Kujenga Post (KP) is one of the most reliable and successful government agencies in the country. | + | Kujenga Post (KP) is one of the most reliable and successful government agencies in the country, providing several government services. Approximately 1530 KP offices are located throughout the country. Services range from delivery of letters and packages to operation of government-funded public transit known as the Dalla Dalla. |
| − | |||
| − | + | Post offices are both government facilities and private franchises. In cities and small towns, each office provides a full range of services including, post of letters and parcels, financial services, express mail, official notary, wholesale and retail offering of SIM and voucher cards, direct advertisement through post boxes, and public transport terminals. | |
| − | + | KP-provided financial services are extensive and go beyond those normally found in western postal systems. KP offices conduct money transfers using phone, fax, local and international money orders. As an official government record office, the KP also makes pension payments, tax collection, and issuance of duty stamps. Incursion of electronic fund transfers using private cell phones threatens this government-controlled system, creating another motivation for the government to control introduction of widely available cell service and the internet for the public. | |
| − | + | Services provided by the KP supply the government with a means of monitoring a broad portion of public activities. Using the KP to track individual movement using the Dalla Dalla, or monitoring the movement of funds internally and internationally, facilitates government monitoring. This condition motivated the government to upgrade and expand KP services, to include sale of SIM cards for cell phones and internet access. | |
| − | + | ||
| − | + | Governmental use of the postal system to monitor activities in the Kasama area of the country caused the AJP to interdict the KP. The group waylaid Dalla Dallas enroute, destroying buses, kidnapping drivers and passengers, and stealing cargoes. Asari-Dokubo claims the interruption of government postal services is an element of AJP’s media campaign, so the group routinely films the events and publishes pleas for help from those kidnapped. | |
=== Word of Mouth === | === Word of Mouth === | ||
| − | As with many African cultures, | + | As with many African cultures, Word of Mouth (WoM) is a mainstay of government, civil, and military communications. WoM maintains an automatic credibility in all family and tribal interactions and associations. There are strong WoM message conduits found throughout most of the country; the strongest in the Kasama and Tanga regions. |
| − | + | ||
| − | Education | + | Education is available to every Kujenga citizen by law. The poor, however, often cannot afford the fees, uniforms, and travel costs for children to attend schools. In addition, the cultural bias towards education of males over females creates a significant gender bias. |
| + | |||
| + | Those students fortunate enough to make their way through the educational system enjoy fully accredited schools and higher-level institutions available. The 23 colleges and universities in Kujenga cover a range of advanced education focused on science, technology, religion, philosophy, medicine and other typical academic studies. | ||
| − | + | Student bodies of higher-level education institutions are often the source of social and political activists. These students and activist groups use word of mouth during rallies, social and print media to deliver their message to the population. As noted earlier, activist groups utilize pirate radio to broadcast their messages, with the government responding by using all available resources to silence them. | |
| − | + | ||
| − | Student bodies of higher-level education institutions are | + | Religious schools are widely available and popular with the population, especially in the Mbeya area of the country. These schools actively include anti-colonial and pro-independence content in their curriculum that supports the AJP. Students are encouraged to support the AJP movement with acts of civil disobedience and resistance to government oppression. |
| − | |||
| − | Religious schools are widely available and popular with the population in the Mbeya area of the country. These schools actively include anti-colonial and pro-independence content in their curriculum that supports the AJP. Students are encouraged to support the AJP movement with acts of civil disobedience and resistance to government oppression. | ||
=== Information Control === | === Information Control === | ||
| − | + | Kujenga’s government justifies its control of the media and restriction of freedom of expression as necessary to ensure national security. The Anti-Terrorism law passed in 2009 contained very broad definitions of terrorism and support to terrorist groups. The law’s vague language granted the government the ability to prosecute individuals and groups publishing anti-government messages. The government continues to expand its use of the law to counter emerging rights advocates groups. Using the law’s authority, the government employs security and military forces to track and arrest dissenting individuals and groups. | |
== INFOWAR == | == INFOWAR == | ||
| − | INFOWAR | + | The Kujenga Intelligence Service (KIS) controls and directs INFOWAR (IW) at the national level. Based on the President’s direction to the National Defense Council, the KIS plans, organizes and conducts INFOWAR operations to support both national objectives as well as providing support to military operations. |
| + | |||
| + | Kujengan National Army (KNA) Directorate of Ground Intelligence coordinates and manages KIS assets once assigned. Assets, primarily from the Signal Reconnaissance Brigade (SRB), deploy on an area support basis or are task organized with maneuver forces as needed. Typically, each of the maneuver divisions will have an INFOWAR battalion included in their task organizational structure sourced from the SRB. The Kujenga Air Force (KNAF) also receives support from the KIS in the form of a Signals and Imagery Squadron. The Kujenga Navy (KNAV), as a brown-water force, does not have organic INFOWAR capability nor does it typically receive support from KIS assets. | ||
| + | |||
| + | KIS forces field older IW systems in support of military and police operations in country. The Signal Reconnaissance Brigade encompasses the main INFOWAR capability of the military. A small company-sized element in the Kujengan Security Corps' (KSEC) Special Reaction Division (SRD) has advanced INFOWAR capability that rises to the Tier 1 level. | ||
=== Electronic Warfare === | === Electronic Warfare === | ||
| − | + | Electronic warfare (EW) capabilities consist mostly of intercept, jamming and direction finding, used largely to disrupt radio and television signals. For military operations, EW systems provide targeting information of threat command and control nodes for targeting and physical destruction. The Signal Reconnaissance Brigade supports military operations with reconnaissance, surveillance, and target acquisition. | |
| + | |||
| + | The KNA employs direction finding and broadband jamming in the Tanga region to disrupt radio broadcasts from the FTYM and Amari. The Information Warfare Battalion supporting the Brigade in the Upper Defense Region passes targeting information for pirate radio transmitters to support the mission of maneuver elements in the capture of Tanga radicals. | ||
=== Computer Attack === | === Computer Attack === | ||
| − | + | Kujenga’s focus on computer attack capabilities was limited until recent international attacks on financial institutions in the country. After the attack, authorities reported estimated losses totaling as much as $85 million. Even though Kujenga’s internet use is limited, that use is concentrated in the government, military, and financial sectors. This provided a strong motivation for the government to create the Kujenga Network Security Authority (KNSA) and the Information System Security Law (ISSL). The KNSA oversees the expansion of information networks within Kujenga, including setting and enforcing security standards. | |
| + | |||
| + | The KNSA launched a program to create a rapid increase in cyber-attack capabilities. With annual financial losses in East Africa expected to top $2 billion a year in the financial sector alone, the government is going on the cyber offensive. Using the theory that to catch a thief you must think like a thief, the government enlisted the aid of Cyber-Troll, cyber security contractors from Nyumba. Little open source information is available about the group other than its main office is located in Nyumba and its web presence offers complete cyber security services for governments and large institutions. Unconfirmed reports are that the government plans to recoup the financial losses by conducting cyber-attacks of Kujenga’s regional competitors. | ||
=== Information Attack === | === Information Attack === | ||
| − | + | Kujenga’s government is widely known for its pervasive surveillance of online and mobile phone communications. A 2014 Human Rights Watch report accused Kujenga’s government of using cyber-attack to monitor and arrest citizens it deemed a threat. Human Rights Watch accused the government of using a monitoring system from the telecommunications firm ZTE (ZXMT) to monitor various communications platforms, including phone and internet networks. ZXMT permits deep-packet inspection and the interception of emails on Kujenga-Telecom's telecommunications network. Kujenga-Telecom has also used ZSmart, a customer management database that provides the monitor with users' personal information, SMS text messages, and the ability to record phone conversations. The ZSmart program can GEOlocate a user's position by tracking mobile cellular devices. The full extent of the government's use of these technologies is unclear; however, the government has produced emails, text messages, and phone calls as evidence during legal proceedings against bloggers and journalists. | |
=== Deception === | === Deception === | ||
| − | + | The KNA uses physical deception measures; active camouflage, concealed forces in structures, and misdirection of observation by using decoys. Faced with primarily internal threats, Kujenga forces do not employ extensive deception during their deployments in support of internal security operations. | |
| + | |||
| + | The Kujengan Security Corps (KSEC) conducts extensive deception during rural border enforcement missions. KSEC assigns internal units or requests additional forces from the KNA to be able to portray the desired appearance in their efforts to entrap FTYM or AJP elements. The deception traps include small convoys, isolated checkpoints, or command and control headquarters to present the appearance of lucrative targets for insurgents. These deception units receive support from aviation assets, indirect fire, and/or mobile quick reaction forces. | ||
| − | === Physical | + | === Physical Attack === |
| − | + | Kujengan doctrine calls for targeting opposition information systems. As computers and communication networks are key elements of international business and government, Kujenga uses either internal capabilities or contracted services to conduct physical attacks. Physical attacks to disrupt or destroy information systems remain the primary means of attack against threat information systems because computer and information attack capabilities are not well developed. Targets include computer operations centers, data storage facilities, network control centers, and other information systems. | |
=== Protection and Security Measures === | === Protection and Security Measures === | ||
| − | + | Kujenga’s leadership, recognizing the cyber threat, instituted in-depth security procedures to protect government, military, and financial systems. They instituted mandatory training and rapid application of software patches, network firmware, and other security measures to protect Kujengan information assets. The limited size of the Kujengan information network worked in the countries favor, as it was simpler to emplace and enforce network security procedures. As the population is relatively new to social media and has not widely adopted it, they are not as susceptible to phishing and other forms of information attack. | |
| − | + | The newly created KNSA oversees the government’s expansion of the information network and public internet access. The KNSA charter tasks it to take all measures necessary to protect the nation’s network systems. The Information System Security Law (ISSL) that directed the creation of the KNSA instituted nation-wide cyber security policy. The ISSL directs mandatory security rules that all service providers and users must follow. Under the law, the KNSA has the authority to charge offenders under the Penal Code and levy punishments ranging from fines up to imprisonment. | |
| − | |||
| − | + | The KNSA is also responsible for developing cyber-attack and defense capabilities. This fiscal year, the government allocated 87 million Euros to support cyber advancements. The KNSA applied a significant portion of that budget towards development of artificial intelligence capability designed to improve network protection and security measures. | |
| − | + | The KNSA is also responsible for ensuring the security of military computer and information systems. KNSA inspectors monitor military compliance with cyber security measures. The government’s focus on compliance with security procedures resulted in removal of several mid-level and one senior officer for failure to follow security requirements. | |
| − | |||
| − | + | === Perception Management === | |
| + | Kujenga’s continuing policy of information control supports its ability to control the perceptions of the population. The intent of the policy is to control the information available to the public and present only the government’s message. Pirate radio broadcasts, increasing availability of satellite television, and increased public access to the internet are challenging the government’s ability to control the flow of information and the resulting population perceptions. As necessary, the government uses disinformation or discrediting of sources to invalidate news reports contrary to the government’s interests. | ||
| − | == | + | == Intelligence == |
| − | + | Kujenga maintains a centralized intelligence organization and allocates assets to military, security, or national missions based on analyzed requirements. The intelligence organization does not produce a strategic threat analysis as the ruling elite hold that role. The President and his close advisors define the national level threat focus and direct allocation of intelligence capabilities as needed. | |
| − | + | The nation uses a broad range of HUMINT, IMINT, SIGINT, and OSINT resources to capture and produce the intelligence products needed to support operations. Available intelligence capabilities and systems are limited to those typical of Tier 2 countries but there are some niche collection systems that rise to the Tier 1 level. | |
| − | + | === Command and Control Systems === | |
| + | * Government | ||
| + | ** Networks - Limited C2 via radio, mainly fixed hard-wire communication | ||
| + | ** Radar - Niche capability with purchase of aerostats for border and regional surveillance | ||
| + | ** Optical - Imagery based on fixed-wing platforms and purchased satellite imagery products | ||
| + | ** Satellite - No organic satellite capability but has standing contracts for on-demand imagery | ||
| + | * Military | ||
| + | ** Networks - C2 network using encrypted radio and fixed landlines | ||
| + | ** Radar - Ground and medium to low altitude coverage using aerostats | ||
| + | ** Radio - Microwave relays, HF, VHF, and UHF frequencies with manual message encryption | ||
| − | + | === Human Intelligence === | |
| + | Human intelligence continues to provide the majority of external data collection and a balanced share of internal intelligence. Kujenga operates a network of HUMINT assets in Amari, primarily based in the criminal, entertainment, and transportation sectors. Agents use the criminal networks, popular entertainment establishments, smuggling and trade routes to collect information deemed critical to Kujenga’s national interests. | ||
| − | + | Internally, KSEC operates tribal agents and informants focused on collecting information on insurgent and separatist groups. These HUMINT assets are both passive information collectors as well as direct action agents that target leaders and organizers of opposition groups. | |
=== Open Source Intelligence === | === Open Source Intelligence === | ||
| − | + | Kujenga is rapidly adopting open source information research and analysis to improve intelligence capabilities with the assistance from Cyber-Troll contractors. The Information Warfare unit of the KSEC received training and support from Cyber-Troll to develop and refine open source intelligence (OSINT) capabilities at the national level. Combining open source collection techniques with the monitoring systems already in place enhances the unit’s capability to track financial transactions tied to insurgent activities. As the information networks expand under the government’s control, the expectation is that the use of OSINT will grow as well. | |
=== Signals Intelligence === | === Signals Intelligence === | ||
| − | + | SIGINT capabilities reside primarily in the Signals Reconnaissance Brigade of the KNA. The Brigade fields a range of systems mostly focused on signals intercept and direction finding. There are active communication and radar jamming systems, but those are held at the national level and do not typically operate with deployed forces of the KNA. | |
| + | |||
| + | Kujenga recently added a man-portable GPS jamming system that is effective against signals in the 4 to 25 Watt range. This system has not deployed with KNA forces; national leadership controls deployment. Indications are that the Kujenga Navy will use the jammers to protect port facilities. | ||
=== Imagery Intelligence === | === Imagery Intelligence === | ||
| − | + | Kujenga’s imagery collection capability is limited to aviation platforms and newly acquired Aerostat platforms. These systems are capable of near real-time collection, depending on mission profile and performance characteristics of the fixed- and rotary-wing aircraft available. High resolution, IR FLIR, and multi-spectral camera arrays are limited in number and are strictly controlled assets. Satellite imagery is a contracted resource limited to national level use and allocation. | |
=== Measurement and Signatures Intelligence === | === Measurement and Signatures Intelligence === | ||
| − | + | Kujenga has no established MASINT systems, but a recent purchase of aerostat-based radar systems for border and regional surveillance provides a niche capability. The aerostat’s radar detects and tracks low-and medium-altitude aircraft, up to 25,000 feet in altitude and 100 nautical miles in range, depending on aerostat height. | |
== Summary == | == Summary == | ||
| − | + | Kujenga maintains a government controlled information environment that uses active monitoring to detect any anti-government message traffic. It follows a strategy of expanding the information systems available to the population while putting in place policies and systems to allow it to control information flow. Current INFOWAR systems provide a reliable level of capabilities with a small segment of the Kujenga Intelligence Service able to employ advanced systems and techniques. | |
| − | [[Category:DATE | + | |
| − | [[Category: | + | [[Category:DATE]] |
| − | [[Category: | + | [[Category:Africa]] |
| + | [[Category:Kujenga]] | ||
[[Category:Information]] | [[Category:Information]] | ||
Latest revision as of 20:20, 2 July 2020
Kujenga ’s information environment is somewhat dated, with limited availability of internet, mobile phone, and television access for the general population. The government is investing in projects to expand internet connectivity but widespread public access is still limited. While Kujenga does have a mix of public and private media available, the government controls much of the media programs available to the public. Kujenga’s information operations utilize mostly low-tech capabilities, along with selected niche capabilities. As a less technically oriented country with narrowly focused modernization goals, information flow remains concentrated on widely available systems. Radio and print media still dominate the Kujenga information sphere. As a country with limited technical information systems, Kujenga is significantly less susceptible to cyber-attacks and information system manipulation. Kujenga’s government seeks to dominate the information sector by controlling the flow of information to the population. To maintain that dominance, the government plans to increase use of new technology and meter its release to the population.
Satellite Telecommunications
Kujenga’s satellite communication capabilities are currently limited to commercial products. Kujenga recently entered into contracts with a company from Torrika to provide a turnkey solution for micro-satellites. Kujenga’s goals are to enhance satellite communications services and to establish satellite-based SIGINT and IMINT capabilities by mid-2019. The contract specifies construction of satellite platforms to Kujenga specifications, launch, and a ground-control complex. Once operational, the satellites will provide Tier-1 command and control communications, signals intercept, and imagery.
Government and military forces have access to GPS capabilities for critical command and control systems and weapons platforms. Limited availability causes Kujengan forces to rely on proven manual navigation techniques not dependent on satellite systems. Kujenga assigns forces on a regional basis for prolonged periods so they are very familiar with the terrain and its characteristics.
Public Communications Media
Kujenga Telecommunications (KT) is the government monopoly controlling the country’s’ communication networks. Private investors can purchase franchises through KT to open businesses providing radio, television, and both wired and wireless internet services. KT provides radio and television and franchises private broadcast services. Contribution of the communication sector to the Kujenga economy is currently only at 2%, significantly below the 4% or higher found in other countries in the East Africa. Kujenga’s government, realizing the potential positive impact on the economy, instituted a strategy to expand services available to the public. As ICT developments come on line, the government expects to rapidly realize economic growth other developing countries experience. This strategy maintains a central requirement to monitor and control the information flow.
The government intercepts and monitors private message traffic across all information systems. It conducts active suppression of media reports critical of the government through network filtering, as well as jamming or interruption of service for the targeted broadcast system. Anti-government activities in the Tanga and southwest region prompted the government to use active measures to disrupt or restrict information flow. The government uses jamming, internet filtering, and destruction of print media in both regions in efforts to suppress the information campaigns of insurgent groups.
Internet
Kujenga’s general population is not technically adept, but has a growing interest in the internet. At 12% penetration, Kujenga has one of the lowest teledensities in the world, largely based on government access restrictions. To maintain control of public information flow, the government methodically works to expand availability of internet access. The government also invests in expansion of the network backbone available in Kujenga. Consistent access is limited to those institutions and organizations that need it for modern business. The government expects the improved business access coupled with other economic development initiatives to help generate at least a 2% GDP growth. The ruling group enjoys mostly unrestricted internet access while the public is only beginning to establish regular connectivity. Internet availability for the public is limited to major cities, with individual access still prohibitively expensive for the average Kujengan.KT is laying the groundwork necessary to allow continued monitoring and control of Kujenga’s internet users. To facilitate this control, the government established the Network Security Agency (NSA) in 2011. The NSA not only issues national internet policies and guidance, but also develops the means to penetrate or block internet communication. The agency restricts targeted internet protocol (IP) addresses or domain names. It also uses deep-packet inspection (DPI) to identify email traffic deemed contrary to the governments’ interests.
Kujenga’s government is widely known for its pervasive surveillance of online and mobile phone communications. A 2014 Human Rights Watch report accused Kujenga’s government of using cyber-attack methods to monitor and arrest citizens it deemed a threat. Human Rights Watch accused the government of using a monitoring system from the telecommunications firm Olvana Telecommunications Enterprise (OTE) to monitor various communications platforms, including phone and internet networks. OTE permits deep-packet inspection and the interception of emails on KT’s telecommunications network. KT also used ZSmart, a customer management database that provides the monitor with users' personal information, SMS text messages, and the ability to record phone conversations. The ZSmart program has the ability to GEOlocate a user's position by tracking mobile cellular devices. The full extent of the government's use of these technologies is unclear. The government, however, has produced emails, text messages, and phone calls as evidence during legal proceedings against bloggers and journalists.
Television
Television access is most common in urban areas. Kujenga is at the lower end of the scale of households with televisions. While slowly growing, the number of households with television currently stands at just over 9%, with a projected growth rate of .5% per year. Any television found in rural areas tends to be a family or tribal asset shared by the group. Some insurgent groups provide television access and programming to support their media strategy, as they provide not only programming of interest but also messages supporting their cause.
Kujenga’s TV stations are both public/government granted private franchises. The government approves program content for public access. Broadcast programming comes from KT, and provides a variety of entertainment, news, sports, and pro-government political commentary. A recent addition of approved private broadcasters providing primarily religious programming is reaching both local and regional audiences. The focus of these broadcasts is to provide the poor and rural population with positive and encouraging programming. These religious programs recently caused a backlash from the Army of Justice and Purity (AJP), who seized a television station at Mbeya in order to broadcast their own message. The AJP stated that both government and private programs were an attempt to co-opt and dilute their message. They held the station and broadcast anti-government messages until overwhelmed by government forces. AJP media elements filmed the brutal and overwhelming government response, creating propaganda supporting its media message. The AJP continues to use all available media resources to carry its message to the Kujengan people.
Radio
Until recently, the government monopolized the radio media environment in Kujenga. The public had no other conduits for independent news or other programming. The advent of pirate radio stations and powerful broadcasts by stations located in bordering countries expanded the public’s knowledge of differing views and perspectives on activities in Kujenga. Recognizing the growing public dissatisfaction with the media status-quo, Kujenga’s government initiated programs to license private radio broadcasts. The result of the program was an expansion from the single government radio network to 22 private broadcasters. Licensed private broadcast networks must follow stringent government controls and regulations, but the expansion is fueling growing public demands for unbiased and differing perspectives for news, sports, entertainment, and politics.
Public and private radio is the most ubiquitous information source available to the public. The government follows the same process with radio as it does with television. KT issues franchises for radio broadcast licenses and approves all programming content. By controlling the broadcast towers and monitoring program content, the government seeks to ensure a consistently positive government message. Deviations from the approved government content by private stations results in suspension of operating licenses for undetermined periods.
The Free Tanga Youth Movement (FTYM) and Army of Justice and Purity (AJP) both utilize pirate radio in their respective regions to broadcast their anti-government message to the population. The government response is blanket jamming of the station signal, use of direction-finding equipment to pinpoint the transmitter locations, and eventually, permanent destruction of the broadcast sources. Faced with this threat from government forces, these groups utilize multiple mobile transmitters with limited broadcast range.
Print Media
Population literacy stands at over 73% so print media holds a very strong position in public information flow. As with the other information mediums, print media must conform to government censorship and monitoring. Of the 12 daily newspapers, 13 weekly newspapers, and 17 national magazines, it is almost certain that one or more of them will be in conflict with the government at any given time.
Print media is generally safe from government reaction when they run stories or reports of bureaucratic mismanagement or inefficiencies. However, reports of suspected corruption by specific ministers or senior leadership often results in shuttered offices for an indeterminate period. Once public attention dies down, government authorities usually allow the offending newspaper or periodical to resume operation.
Recalcitrant journalists that fail to conform to government guidelines often find themselves jailed under some, often obscure, aspect of the law. The Press Law of 1987 allows the government to suppress news reports or stories that are detrimental to national interests, modifying the constitutional guarantee of freedom of press.
The growth of the internet and social media is pressuring physical print media businesses. Growth projections for mobile phones and internet access are driving the print media businesses and groups to expand their reach into the social media sphere. Printers are seeking additional markets to remain viable in the changing environment. Many are transferring their knowledge and skill in developing meaningful message products to the new information media.
Government opposition groups are currently the most active users of social media. They use it to send handbills and infographic bulletins to followers and sympathizers in Kujenga, neighboring countries, and expatriates. To develop successful messages, the groups are working with print media companies to produce professional products.
Telephone
If a Kujengan has a phone, it is a mobile phone. As with many other countries in Africa, the population generally bypassed fixed landline phones. Comparison of landline to mobile subscribers sees 1% and 25% per 100 citizens, respectively. Mobile subscribers are mostly the ruling elite, business leaders, and military leadership. Major cities and urban areas have the greatest concentrations of mobile phone coverage, with limited coverage along the main roads between cities. Laws prohibit private satellite phones; government customs officers confiscate them at all entry points.
Kujengans are aware of the technological advancements in communication technology. Until recently, the government limited the expansion of the mobile phone networks available. The government views mobile technology as a threat to its control and direction of the population. It views outside attempts by groups in Amari and Ziwa to extend technology and information to the Kujenga population as a direct threat to its control and power.
Reports and studies show that mobile phone and internet access in African countries stands at over 1 billion. Projections suggest it will jump to 1.4 billion subscribers in the next 5 years. This led the Kujengan government to conclude that expansion is inevitable. That perceived inevitability is driving the government to take proactive steps to expand the mobile phone network while it can still control that expansion.
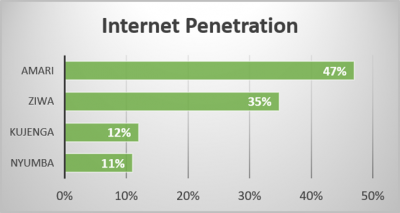
Current subscriber levels are approximately 25%, which puts Kujenga a distant third behind Ziwa and Amari in mobile phone penetration of the population. The predicted availability of low-cost mobile phones, data packages, and the government expansion of available mobile networks creates the conditions for the subscriber population to exceed 50% by 2022. The government is not only expanding the mobile networks but also its capability to monitor and track citizen activities using commercial off-the-shelf (COTS) software and hardware.
Postal/Courier
Kujenga Post (KP) is one of the most reliable and successful government agencies in the country, providing several government services. Approximately 1530 KP offices are located throughout the country. Services range from delivery of letters and packages to operation of government-funded public transit known as the Dalla Dalla.
Post offices are both government facilities and private franchises. In cities and small towns, each office provides a full range of services including, post of letters and parcels, financial services, express mail, official notary, wholesale and retail offering of SIM and voucher cards, direct advertisement through post boxes, and public transport terminals.
KP-provided financial services are extensive and go beyond those normally found in western postal systems. KP offices conduct money transfers using phone, fax, local and international money orders. As an official government record office, the KP also makes pension payments, tax collection, and issuance of duty stamps. Incursion of electronic fund transfers using private cell phones threatens this government-controlled system, creating another motivation for the government to control introduction of widely available cell service and the internet for the public.
Services provided by the KP supply the government with a means of monitoring a broad portion of public activities. Using the KP to track individual movement using the Dalla Dalla, or monitoring the movement of funds internally and internationally, facilitates government monitoring. This condition motivated the government to upgrade and expand KP services, to include sale of SIM cards for cell phones and internet access.
Governmental use of the postal system to monitor activities in the Kasama area of the country caused the AJP to interdict the KP. The group waylaid Dalla Dallas enroute, destroying buses, kidnapping drivers and passengers, and stealing cargoes. Asari-Dokubo claims the interruption of government postal services is an element of AJP’s media campaign, so the group routinely films the events and publishes pleas for help from those kidnapped.
Word of Mouth
As with many African cultures, Word of Mouth (WoM) is a mainstay of government, civil, and military communications. WoM maintains an automatic credibility in all family and tribal interactions and associations. There are strong WoM message conduits found throughout most of the country; the strongest in the Kasama and Tanga regions.
Education is available to every Kujenga citizen by law. The poor, however, often cannot afford the fees, uniforms, and travel costs for children to attend schools. In addition, the cultural bias towards education of males over females creates a significant gender bias.
Those students fortunate enough to make their way through the educational system enjoy fully accredited schools and higher-level institutions available. The 23 colleges and universities in Kujenga cover a range of advanced education focused on science, technology, religion, philosophy, medicine and other typical academic studies.
Student bodies of higher-level education institutions are often the source of social and political activists. These students and activist groups use word of mouth during rallies, social and print media to deliver their message to the population. As noted earlier, activist groups utilize pirate radio to broadcast their messages, with the government responding by using all available resources to silence them.
Religious schools are widely available and popular with the population, especially in the Mbeya area of the country. These schools actively include anti-colonial and pro-independence content in their curriculum that supports the AJP. Students are encouraged to support the AJP movement with acts of civil disobedience and resistance to government oppression.
Information Control
Kujenga’s government justifies its control of the media and restriction of freedom of expression as necessary to ensure national security. The Anti-Terrorism law passed in 2009 contained very broad definitions of terrorism and support to terrorist groups. The law’s vague language granted the government the ability to prosecute individuals and groups publishing anti-government messages. The government continues to expand its use of the law to counter emerging rights advocates groups. Using the law’s authority, the government employs security and military forces to track and arrest dissenting individuals and groups.
INFOWAR
The Kujenga Intelligence Service (KIS) controls and directs INFOWAR (IW) at the national level. Based on the President’s direction to the National Defense Council, the KIS plans, organizes and conducts INFOWAR operations to support both national objectives as well as providing support to military operations.
Kujengan National Army (KNA) Directorate of Ground Intelligence coordinates and manages KIS assets once assigned. Assets, primarily from the Signal Reconnaissance Brigade (SRB), deploy on an area support basis or are task organized with maneuver forces as needed. Typically, each of the maneuver divisions will have an INFOWAR battalion included in their task organizational structure sourced from the SRB. The Kujenga Air Force (KNAF) also receives support from the KIS in the form of a Signals and Imagery Squadron. The Kujenga Navy (KNAV), as a brown-water force, does not have organic INFOWAR capability nor does it typically receive support from KIS assets.
KIS forces field older IW systems in support of military and police operations in country. The Signal Reconnaissance Brigade encompasses the main INFOWAR capability of the military. A small company-sized element in the Kujengan Security Corps' (KSEC) Special Reaction Division (SRD) has advanced INFOWAR capability that rises to the Tier 1 level.
Electronic Warfare
Electronic warfare (EW) capabilities consist mostly of intercept, jamming and direction finding, used largely to disrupt radio and television signals. For military operations, EW systems provide targeting information of threat command and control nodes for targeting and physical destruction. The Signal Reconnaissance Brigade supports military operations with reconnaissance, surveillance, and target acquisition.
The KNA employs direction finding and broadband jamming in the Tanga region to disrupt radio broadcasts from the FTYM and Amari. The Information Warfare Battalion supporting the Brigade in the Upper Defense Region passes targeting information for pirate radio transmitters to support the mission of maneuver elements in the capture of Tanga radicals.
Computer Attack
Kujenga’s focus on computer attack capabilities was limited until recent international attacks on financial institutions in the country. After the attack, authorities reported estimated losses totaling as much as $85 million. Even though Kujenga’s internet use is limited, that use is concentrated in the government, military, and financial sectors. This provided a strong motivation for the government to create the Kujenga Network Security Authority (KNSA) and the Information System Security Law (ISSL). The KNSA oversees the expansion of information networks within Kujenga, including setting and enforcing security standards.
The KNSA launched a program to create a rapid increase in cyber-attack capabilities. With annual financial losses in East Africa expected to top $2 billion a year in the financial sector alone, the government is going on the cyber offensive. Using the theory that to catch a thief you must think like a thief, the government enlisted the aid of Cyber-Troll, cyber security contractors from Nyumba. Little open source information is available about the group other than its main office is located in Nyumba and its web presence offers complete cyber security services for governments and large institutions. Unconfirmed reports are that the government plans to recoup the financial losses by conducting cyber-attacks of Kujenga’s regional competitors.
Information Attack
Kujenga’s government is widely known for its pervasive surveillance of online and mobile phone communications. A 2014 Human Rights Watch report accused Kujenga’s government of using cyber-attack to monitor and arrest citizens it deemed a threat. Human Rights Watch accused the government of using a monitoring system from the telecommunications firm ZTE (ZXMT) to monitor various communications platforms, including phone and internet networks. ZXMT permits deep-packet inspection and the interception of emails on Kujenga-Telecom's telecommunications network. Kujenga-Telecom has also used ZSmart, a customer management database that provides the monitor with users' personal information, SMS text messages, and the ability to record phone conversations. The ZSmart program can GEOlocate a user's position by tracking mobile cellular devices. The full extent of the government's use of these technologies is unclear; however, the government has produced emails, text messages, and phone calls as evidence during legal proceedings against bloggers and journalists.
Deception
The KNA uses physical deception measures; active camouflage, concealed forces in structures, and misdirection of observation by using decoys. Faced with primarily internal threats, Kujenga forces do not employ extensive deception during their deployments in support of internal security operations.
The Kujengan Security Corps (KSEC) conducts extensive deception during rural border enforcement missions. KSEC assigns internal units or requests additional forces from the KNA to be able to portray the desired appearance in their efforts to entrap FTYM or AJP elements. The deception traps include small convoys, isolated checkpoints, or command and control headquarters to present the appearance of lucrative targets for insurgents. These deception units receive support from aviation assets, indirect fire, and/or mobile quick reaction forces.
Physical Attack
Kujengan doctrine calls for targeting opposition information systems. As computers and communication networks are key elements of international business and government, Kujenga uses either internal capabilities or contracted services to conduct physical attacks. Physical attacks to disrupt or destroy information systems remain the primary means of attack against threat information systems because computer and information attack capabilities are not well developed. Targets include computer operations centers, data storage facilities, network control centers, and other information systems.
Protection and Security Measures
Kujenga’s leadership, recognizing the cyber threat, instituted in-depth security procedures to protect government, military, and financial systems. They instituted mandatory training and rapid application of software patches, network firmware, and other security measures to protect Kujengan information assets. The limited size of the Kujengan information network worked in the countries favor, as it was simpler to emplace and enforce network security procedures. As the population is relatively new to social media and has not widely adopted it, they are not as susceptible to phishing and other forms of information attack.
The newly created KNSA oversees the government’s expansion of the information network and public internet access. The KNSA charter tasks it to take all measures necessary to protect the nation’s network systems. The Information System Security Law (ISSL) that directed the creation of the KNSA instituted nation-wide cyber security policy. The ISSL directs mandatory security rules that all service providers and users must follow. Under the law, the KNSA has the authority to charge offenders under the Penal Code and levy punishments ranging from fines up to imprisonment.
The KNSA is also responsible for developing cyber-attack and defense capabilities. This fiscal year, the government allocated 87 million Euros to support cyber advancements. The KNSA applied a significant portion of that budget towards development of artificial intelligence capability designed to improve network protection and security measures.
The KNSA is also responsible for ensuring the security of military computer and information systems. KNSA inspectors monitor military compliance with cyber security measures. The government’s focus on compliance with security procedures resulted in removal of several mid-level and one senior officer for failure to follow security requirements.
Perception Management
Kujenga’s continuing policy of information control supports its ability to control the perceptions of the population. The intent of the policy is to control the information available to the public and present only the government’s message. Pirate radio broadcasts, increasing availability of satellite television, and increased public access to the internet are challenging the government’s ability to control the flow of information and the resulting population perceptions. As necessary, the government uses disinformation or discrediting of sources to invalidate news reports contrary to the government’s interests.
Intelligence
Kujenga maintains a centralized intelligence organization and allocates assets to military, security, or national missions based on analyzed requirements. The intelligence organization does not produce a strategic threat analysis as the ruling elite hold that role. The President and his close advisors define the national level threat focus and direct allocation of intelligence capabilities as needed.
The nation uses a broad range of HUMINT, IMINT, SIGINT, and OSINT resources to capture and produce the intelligence products needed to support operations. Available intelligence capabilities and systems are limited to those typical of Tier 2 countries but there are some niche collection systems that rise to the Tier 1 level.
Command and Control Systems
- Government
- Networks - Limited C2 via radio, mainly fixed hard-wire communication
- Radar - Niche capability with purchase of aerostats for border and regional surveillance
- Optical - Imagery based on fixed-wing platforms and purchased satellite imagery products
- Satellite - No organic satellite capability but has standing contracts for on-demand imagery
- Military
- Networks - C2 network using encrypted radio and fixed landlines
- Radar - Ground and medium to low altitude coverage using aerostats
- Radio - Microwave relays, HF, VHF, and UHF frequencies with manual message encryption
Human Intelligence
Human intelligence continues to provide the majority of external data collection and a balanced share of internal intelligence. Kujenga operates a network of HUMINT assets in Amari, primarily based in the criminal, entertainment, and transportation sectors. Agents use the criminal networks, popular entertainment establishments, smuggling and trade routes to collect information deemed critical to Kujenga’s national interests.
Internally, KSEC operates tribal agents and informants focused on collecting information on insurgent and separatist groups. These HUMINT assets are both passive information collectors as well as direct action agents that target leaders and organizers of opposition groups.
Open Source Intelligence
Kujenga is rapidly adopting open source information research and analysis to improve intelligence capabilities with the assistance from Cyber-Troll contractors. The Information Warfare unit of the KSEC received training and support from Cyber-Troll to develop and refine open source intelligence (OSINT) capabilities at the national level. Combining open source collection techniques with the monitoring systems already in place enhances the unit’s capability to track financial transactions tied to insurgent activities. As the information networks expand under the government’s control, the expectation is that the use of OSINT will grow as well.
Signals Intelligence
SIGINT capabilities reside primarily in the Signals Reconnaissance Brigade of the KNA. The Brigade fields a range of systems mostly focused on signals intercept and direction finding. There are active communication and radar jamming systems, but those are held at the national level and do not typically operate with deployed forces of the KNA.
Kujenga recently added a man-portable GPS jamming system that is effective against signals in the 4 to 25 Watt range. This system has not deployed with KNA forces; national leadership controls deployment. Indications are that the Kujenga Navy will use the jammers to protect port facilities.
Imagery Intelligence
Kujenga’s imagery collection capability is limited to aviation platforms and newly acquired Aerostat platforms. These systems are capable of near real-time collection, depending on mission profile and performance characteristics of the fixed- and rotary-wing aircraft available. High resolution, IR FLIR, and multi-spectral camera arrays are limited in number and are strictly controlled assets. Satellite imagery is a contracted resource limited to national level use and allocation.
Measurement and Signatures Intelligence
Kujenga has no established MASINT systems, but a recent purchase of aerostat-based radar systems for border and regional surveillance provides a niche capability. The aerostat’s radar detects and tracks low-and medium-altitude aircraft, up to 25,000 feet in altitude and 100 nautical miles in range, depending on aerostat height.
Summary
Kujenga maintains a government controlled information environment that uses active monitoring to detect any anti-government message traffic. It follows a strategy of expanding the information systems available to the population while putting in place policies and systems to allow it to control information flow. Current INFOWAR systems provide a reliable level of capabilities with a small segment of the Kujenga Intelligence Service able to employ advanced systems and techniques.